Overview
Assumed: SDL (Software Development Lifecycle) and Change management assumed.
Workflow:
Coders need to ensure they perform test (secure coding practices) on their code before moving it to a Web Server. - https://www.owasp.org/index.php/SWAMP_OWASP
https://snyk.io/product/open-source-security-management/
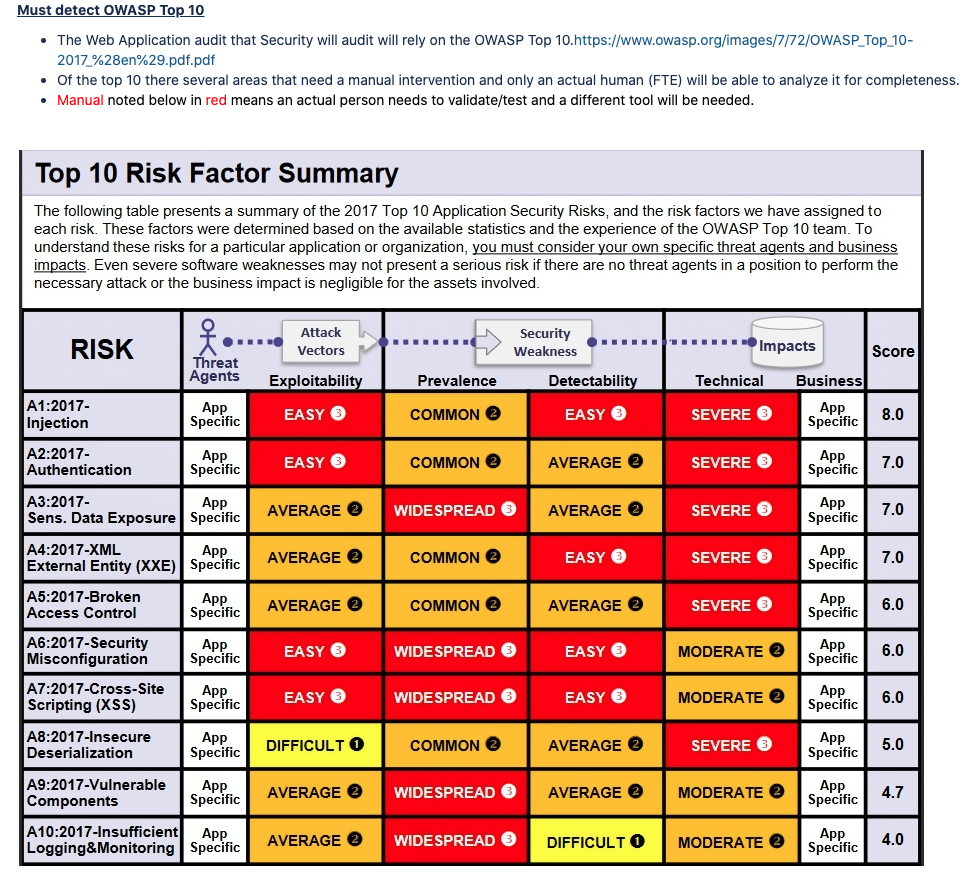
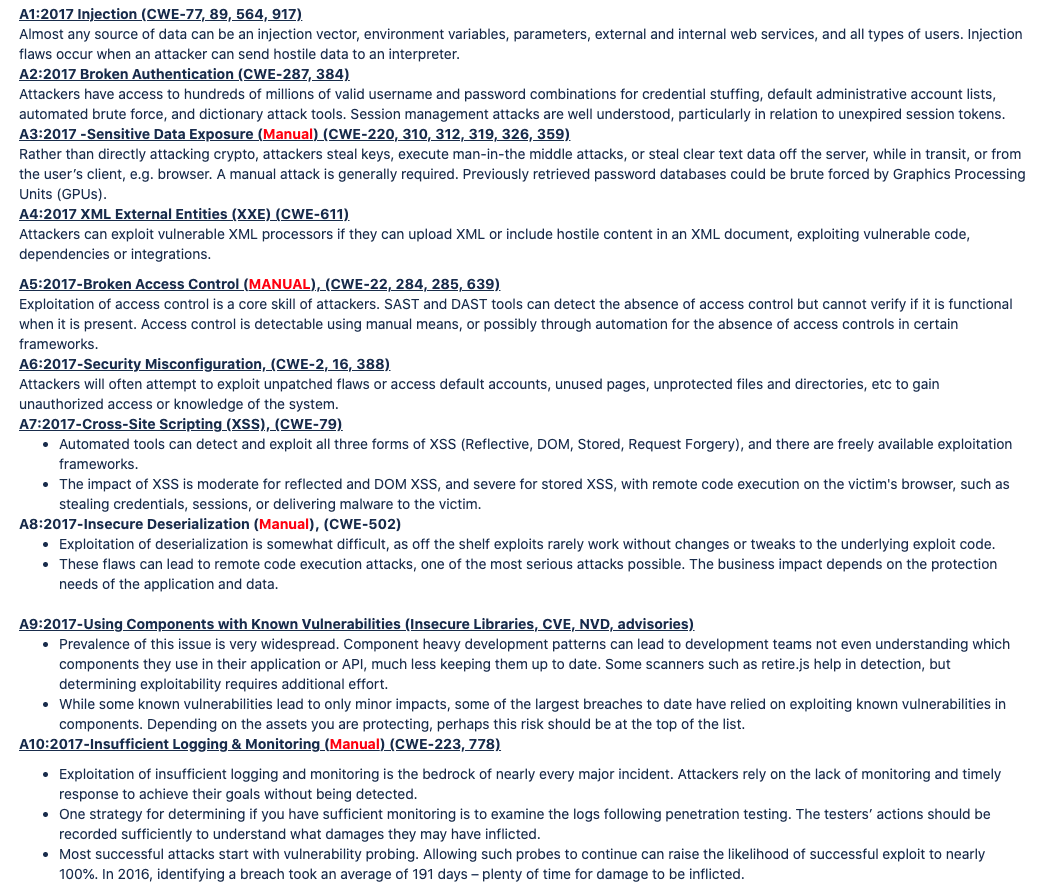
Once a server is built and web app is installed on it then the owners of Web Application may use a Web App scanning tool to ensure OWASP 10 (2017) is effective. https://www.owasp.org/images/7/72/OWASP_Top_10-2017_%28en%29.pdf.pdf
The server the Web Application lives also needs to be included in patch management to ensure it doesn’t have security flaws. (the server will find its way to another security process for auditing network services for Operating System (OS) level and OS level applications such as Java) This should be a cyclic (regularly repeated) as new code is developed and pushed to Web App.
Security can do audits on a monthly/Annual basis (However this should be based off Risk Team findings of riskiest WebApps to business) and send reports of findings to owners of Web Apps
Risk team in Security will review Web App Security audit findings and determine if a Risk needs to be registered and or elevated to senior leadership for consideration as it may be patient impacting with sever consequences to Orgs brand.
**Low Hanging Fruit (LHF) Web App PenTest **
**Requirement: **
Push button and scan large set of Web Apps for OWASP top 10 vulns.
Tools:
Netsparker
BurpSuite Pro (AutoScan)
Arachni
Open Source Github tools, Kali tools, Gobuster, nikto, nmap, ZapProxy, AMASS, etc
Distrusted SSL Certs: https://www.ssllabs.com/ssltest/
**Assumptions: **
Feed reports into Risk for risk assessments (reports are very manual and do not scale-Takes a FTE to manual submit for each website)
This is not an operational endeavor, it’s a governance audit.
This is ONLY an audit of Web Application Pentest Security for use for Risk to create remediation’s and Risk Registry entries as required.
Lower mean-time to detection and remediation of technical flaws in WebApps. <– however this should get push down to Developers and secure coding and web app scans they do themselves.
Will NOT Scale to entire Organization Public facing Web Apps since we have one of everything and we will be using a one size fits all approach with LHF detection.
Will sacrifice in-depth comprehensive Web App pentest in favor of doing only low hanging fruit auto-scans that doesn’t test everything including requirement of manual tests where an actual person needs to do.
The Web Apps we test may go down. Better us than someone else I suppose.
Eventually Dev teams need to have secure code practices and web app security scans baked into their SDLC.
**Reference baseline info around Web App Pentest **
https://www.troyhunt.com/automating-web-security-reviews-with/
https://www.netsparker.com/blog/web-security/how-to-evaluate-web-application-security-scanners-tools/
https://www.owasp.org/images/b/b0/OWASP_Top_10_2017_RC2_Final.pdf